Tools Used
- IDA Pro
Sample:
- Lab07-03.exe SHA256: 3475ce2e4aaa555e5bbd0338641dd411c51615437a854c2cb24b4ca2c048791a
- Lab08-03.dll SHA256: f50e42c8dfaab649bde0398867e930b86c2a599e8db83b8260393082268f2dba
VirusTotal:
- Detection Rate: 23/54(1) & 17/55(2)
- Analyzed on 2016-03-03
-
Compilation Date: 2010-12-19 16:16:19 (1) & 2010-12-19 16:16:38(2)
- View report here(1) & here(2)
Lab 7-3
For this lab, we obtained the malicious executable, Lab07-03.exe, and DLL,
Lab07-03.dll, prior to executing. This is important to note because the malware
might change once it runs. Both files were found in the same directory
on the victim machine. If you run the program, you should ensure that both
files are in the same directory on the analysis machine. A visible IP string
beginning with 127 (a loopback address) connects to the local machine. (In
the real version of this malware, this address connects to a remote machine,
but we’ve set it to connect to localhost to protect you.)
WARNING This lab may cause considerable damage to your computer and may be difficult to remove once installed. Do not run this file without a virtual machine with a snapshot
taken prior to execution.
This lab may be a bit more challenging than previous ones. You’ll need
to use a combination of static and dynamic methods, and focus on the big
picture in order to avoid getting bogged down by the details.
This Lab is the same as Lab01-01. You may find a detail analysis of the binaries in Lab01-01. Back then we concluded that the malware will make a copy of its malicious dll by disguising itself as kerne(1)32.dll. The malware will then try to search for some files and infect it to run this dll. The dll is capable of ensuring that only one instance of the malicious code is running since mutex is being used. It will then communicates on a timely basis (Sleep) to the C&C @ 127.26.152.13 to receive commands to execute on the victim’s machine.
As this malware sample will overwrite existing exe, the author add in some security mechanism to prevent accidental double clicking of the malware. You will need to pass in the following argument “WARNING_THIS_WILL_DESTROY_YOUR_MACHINE” in order for the executable to run.
Questions
1. How does this program achieve persistence to ensure that it continues
running when the computer is restarted?
Based on the analysis done in Lab 01, we know that persistency is achieved via infecting other executable to run kerne(1)32.dll. But back in Lab 01, I did not specifically answer how this is done.
In Lab07-03.exe, @address 0x004010A0, I name this function modifyEXE. If we look at flow graph, we can see that the malware is mapping a file in memory with dwDesiredAccess set to 0x0F001Fh (File Map All Access). Changes made to the mapped view of the file in memory will cause the physical file to change as well.
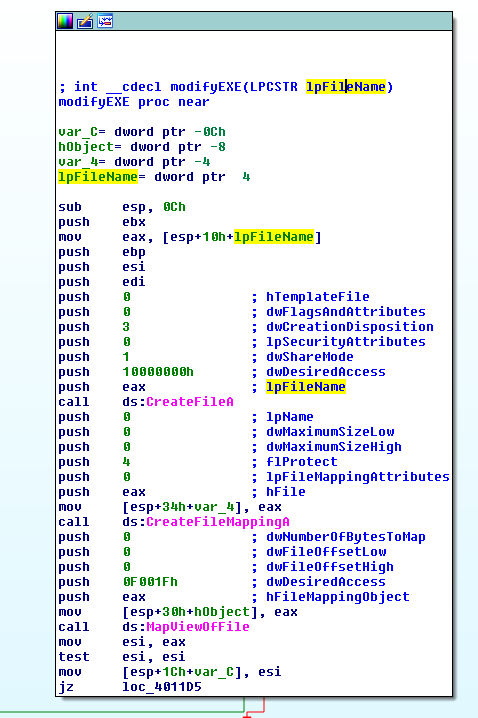
scrolling further down we will come across the following opcodes.
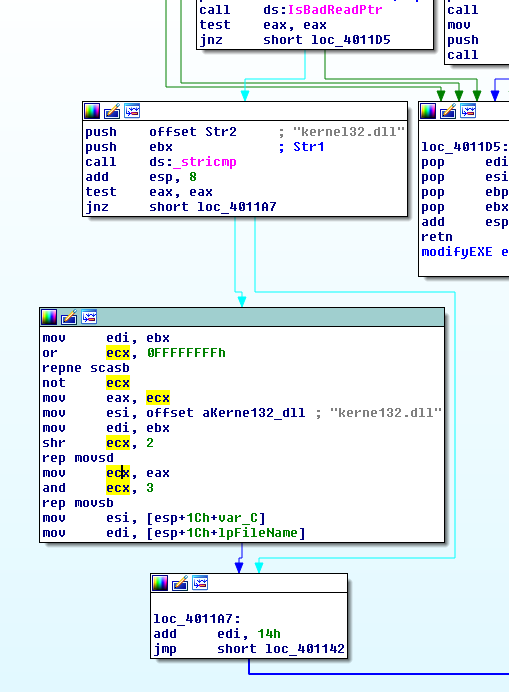
From the above, we can see that the malware is doing a stricmp with its import libraries and the string kernel32.dll, if it matches, the malware will get the strlen of the string via scasb opcode and replaces kernel32.dll with “kerne132.dll” using movsd opcode. When the computer restarts, and an infected executable gets executed, the malicious “kerne132.dll” will get executed as well.
2. What are two good host-based signatures for this malware?
As mentioned in Lab 01-01, the dll uses a unique hard coded mutex “SADFHUHF” and the malicious dll is copied into a hard coded path “c:\windows\system32\kerne132.dll“. We can use these as the host-based signatures.
3. What is the purpose of this program?
The malware will make a copy of its malicious dll in c:\windows\system32\ by disguising itself as kerne(1)32.dll. The malware will then traverse the system looking out for .exe files and infecting it by changing its import library from kernel32.dll to kerne132.dll. This will cause the malicious dll to be executed whenever the infected exe is executed. The dll is capable of ensuring that only one instance of the malicious code is running since mutex(SADFHUHF) is being used. It will then communicates on a timely basis (Sleep) to the C&C @ 127.26.152.13 to receive commands to execute on the victim’s machine.
4. How could you remove this malware once it is installed?
- Patched the above malware to make it search for kerne132.dll in exe and replace it with kernel32.dll. Make a copy of the original kernel32.dll as kerne132.dll just in case that some binaries did not get repaired…
- Restore the entire system as it is not easy to remove the malware from the system.