Took me a week to complete 2 tracks in Palo Alto CTF, Windows and Docs. Will be sharing my humble little solutions here. Hope you guys will learn something useful here. Some of the challenges uses malware techniques! Kudos to the organizer.
File: AntiD.exe
SHA256: 49f3638065722b96809cb72c226d86566783d510c968d516436aa7c248d608ee
Packed: Custom UPX
Tools used: ExeInfo, IDA Pro, Ollydbg, Scylla & CFF Explorer
Codes & Binaries: https://github.com/jmprsp/labyrenth/tree/master/Window-Challenge-1
Description: This challenge uses UPX to pack but modded it to prevent upx -d from working. It also uses some anti debugging techniques to deter the use of debugging tools. Flag is not in clear, one would need to analyze the math behind and decode the flag.
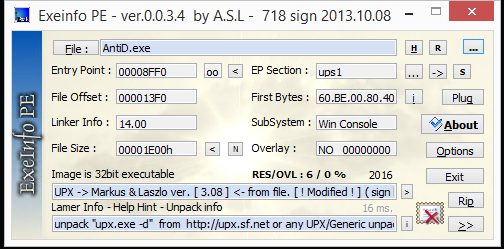
It seems like the binary is packed with UPX. Let’s try to use the official tool to unpack. However it seems like we are unable to unpack =(
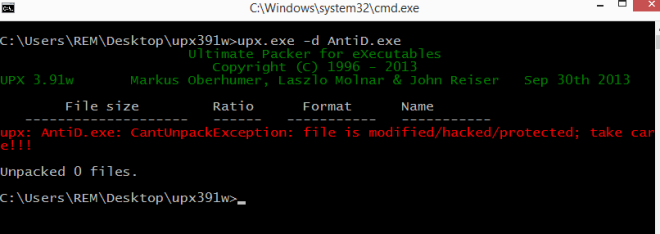
Loading the binary in IDA Pro, we can observe that the binary is indeed packed. From the screenshot below, we can only see 1 function; an indication of a packed binary. Next, we can clearly see that there is a tail jump. To unpack this binary manually, we just need to break at the tail jump and dump the process.
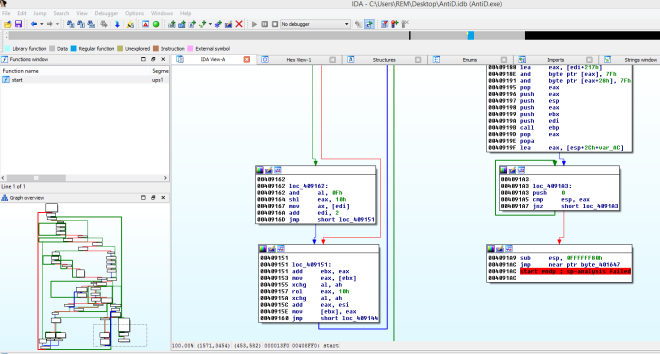
But before that, I would want to disable ASLR to make my job easier while debugging it. Using CFF Explorer tool, simply uncheck “DLL can move” checkbox and apply the changes.
Run the patched AntiD.exe in ollydbg. Set a breakpoint @ 0x4091AC. Run the program till it breaks and step into the next instruction.
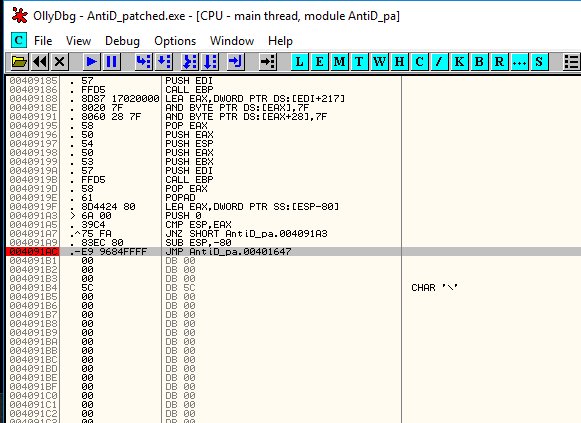
Just dump the process as shown below. However running the dumped process would popup an error.
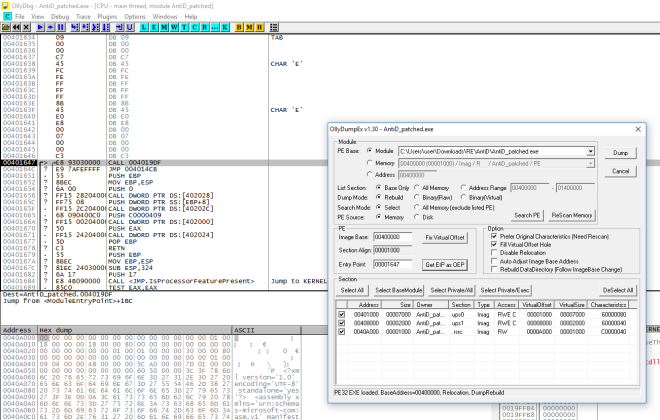
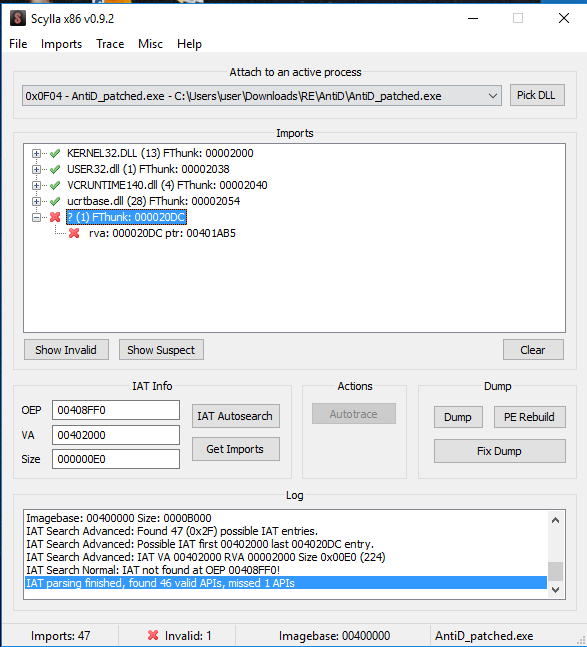
The dumped process’s IAT need to be fixed. For this, I use Scylla tool to delete the invalid imports and clicking on the fix dump button. Now we should have a working copy of the binary.
Loading the unpacked binary into IDA Pro, we can see that it looks unpack now. We can see more functions, imports and plain string.
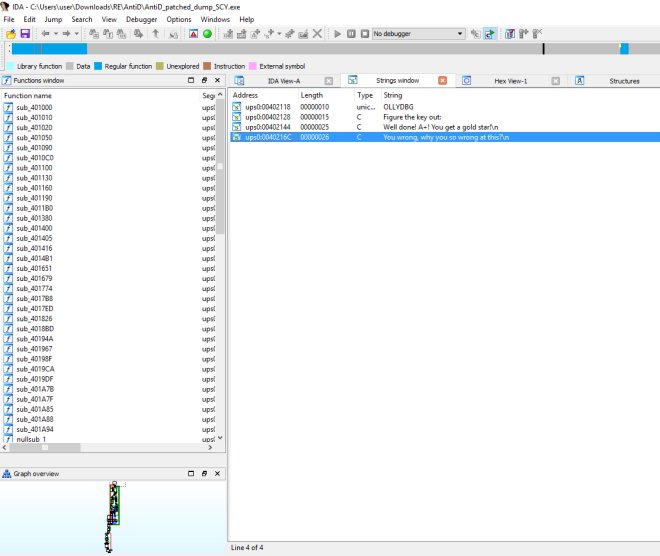
X-referencing from the string, we would derive to the following function. Seems like 0x004011B0 function is the key to solving this puzzle.
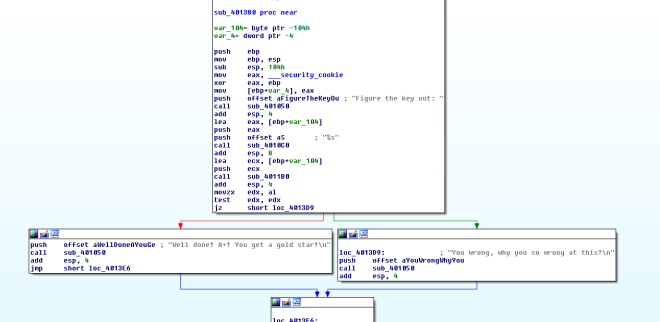
In 0x004011B0 function, we can see some encoded variables; 40 of them and the following mathematical transformation consisting of XOR, addition and subtraction.
I simply converted the codes into PHP and attempt to bruteforce the flag.
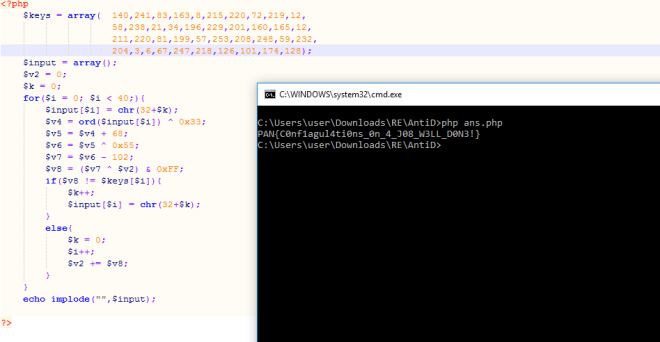
FLAG: PAN{C0nf1agul4ti0ns_0n_4_J08_W3LL_D0N3!}
[…] 本文转载自 jmprsp原文链接:https://jmprsp.wordpress.com/2016/08/31/labyrenth-windows-track-challenge-1/ […]
LikeLike